Exfiltration d'agent (Network Challenge Writeup) -- Midnightflag INFEKTION 2022
Midnightflag Team has elaborated a very entertaining and fun CTF named INFEKTION with a specific theme and even an excellent an spectacular Teaser too. We are especially interested in the forensic and networking challenges, particularly this networking challenge seemed very interesting for dealing with information exfiltration issues.
Challenges Description:
We were given a file to download (source here)
We start opening the file using Wireshark, after analyzing each protocol, we noticed strange hexadecimals characters in the ICMP data field.
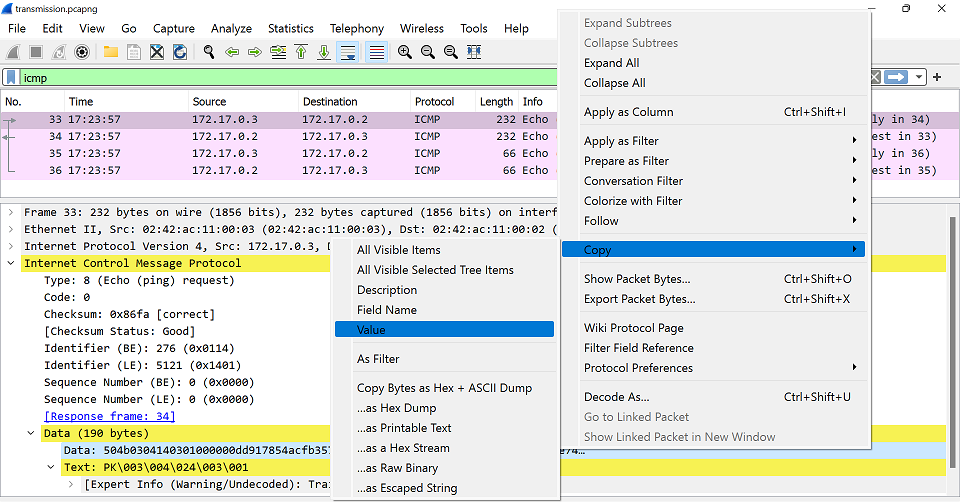
Proceed to copy the string and try to decode it using CyberChef
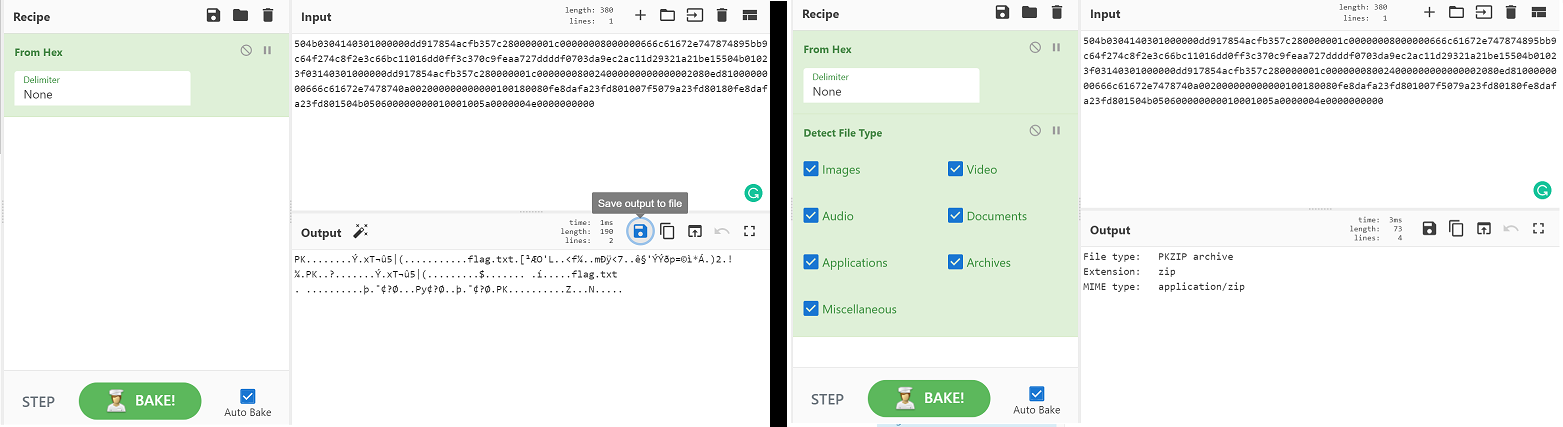
After decoding “from HEX”, cybercheff detects a ZIP file, we proceed to download it with the name chall.zip
the file was encrypted, we use fcrackzip to crack the file.
┌──(leonuz㉿sniper)-[~/Midnightflag/networking/Exfiltration_dAgent]
└─$ fcrackzip -u -D -p /usr/share/wordlists/rockyou.txt chall.zip
PASSWORD FOUND!!!!: pw == G3ars0fwarAfter a few minutes, we find the password!
then we open the zip file using that password…
┌──(leonuz㉿sniper)-[~/Midnightflag/networking/Exfiltration_dAgent]
└─$ 7z x download.zip
7-Zip [64] 16.02 : Copyright (c) 1999-2016 Igor Pavlov : 2016-05-21
p7zip Version 16.02
Scanning the drive for archives:
1 file, 190 bytes (1 KiB)
Extracting archive: chall.zip
--
Path = chall.zip
Type = zip
Physical Size = 190
Enter password (will not be echoed):
Everything is Ok
Size: 28
Compressed: 190and finally, we have the flag inside the txt file!!
┌──(leonuz㉿sniper)-[~/Midnightflag/networking/Exfiltration_dAgent]
└─$ cat flag.txt
MCTF{g00d_0ld_1cmp_pr070c0l}MCTF{g00d_0ld_1cmp_pr070c0l}
Final Notes.
Thanks MidnightFlag Team for the oportunity of a excellent CTF.
Give us more time for the next CTF please!!
For fun and knowledge, always think out of the box! :)