
Intruder (Misc Challenge Writeup) -- CTF GDG Algiers 2022
The GDG Algiers one of the largest community of developers and tech enthusiasts in Algeria and MENA region, has organized the first edition of the GDG Algiers CTF. Competition started October 7 and finish 48 hours later. Was a very fun and hard CTF, with some medium challenges. Very good infra and support. We chose this misc challenge, because it's a clever way to hide info inside an image.
Challenge Description:
File to download (source here)
We start analyzing the image with Online Steganography tools as aperisolve and fotoforensics and local tools as stegsolve and zsteg) without any apparent result.
Then we started to analyze the file with a forensic tools called binwalk and these are the results:
┌──(leonuz㉿sniperhack)-[~/…/ctf/gdgalgiers/misc/intruder]
└─$ binwalk -e AK.png
DECIMAL HEXADECIMAL DESCRIPTION
--------------------------------------------------------------------------------
0 0x0 PNG image, 1024 x 370, 8-bit/color RGBA, non-interlaced
96 0x60 Zlib compressed data, best compression
223958 0x36AD6 Zlib compressed data, default compression
┌──(leonuz㉿sniperhack)-[~/…/ctf/gdgalgiers/misc/intruder]
└─$ ls -la
total 236
drwxr-xr-x 4 leonuz leonuz 4096 Oct 9 18:22 .
drwxr-xr-x 6 leonuz leonuz 4096 Oct 8 17:12 ..
-rw-r--r-- 1 leonuz leonuz 224842 Oct 7 12:30 AK.png
drwxr-xr-x 2 leonuz leonuz 4096 Oct 9 18:22 _AK.png.extracted
┌──(leonuz㉿sniperhack)-[~/…/ctf/gdgalgiers/misc/intruder]
└─$ cd _AK.png.extracted
┌──(leonuz㉿sniperhack)-[~/…/gdgalgiers/misc/intruder/_AK.png.extracted]
└─$ ls
36AD6 36AD6.zlib 60 60.zlib
┌──(leonuz㉿sniperhack)-[~/…/gdgalgiers/misc/intruder/_AK.png.extracted]
└─$ file *
36AD6: ASCII text, with very long lines (24642), with no line terminators
36AD6.zlib: zlib compressed data
60: empty
60.zlib: zlib compressed dataWe find a text file called 36AD6
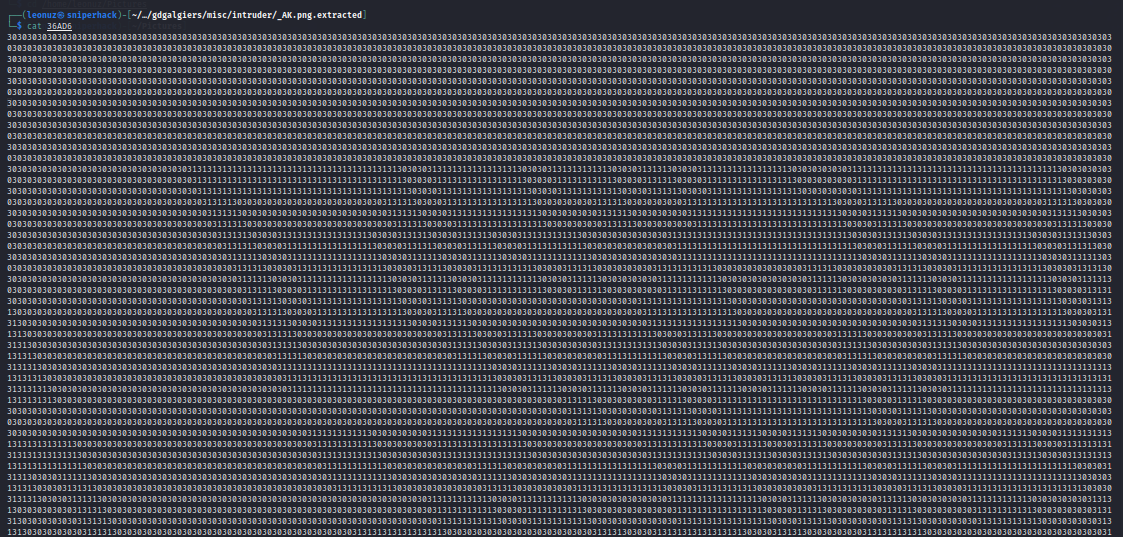
We can see a pattern where the characters “31” are, let’s clean it up a bit, converting those “31” into spaces
┌──(leonuz㉿sniperhack)-[~/…/gdgalgiers/misc/intruder/_AK.png.extracted]
└─$ sed -i 's/31/ /g' 36AD6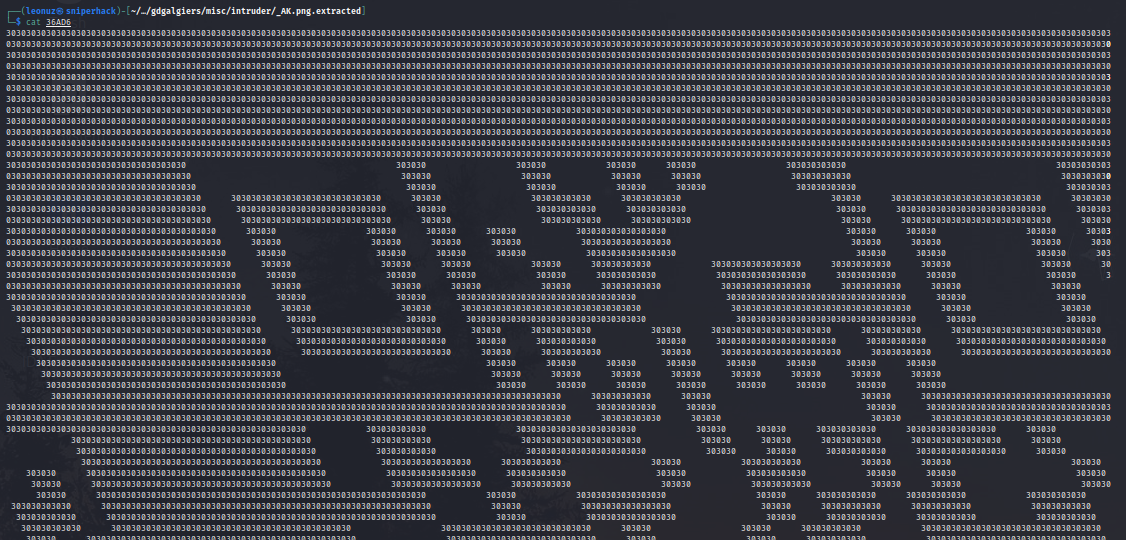
Ok, we have a QR code. Now let’s play a bit with columns and rows
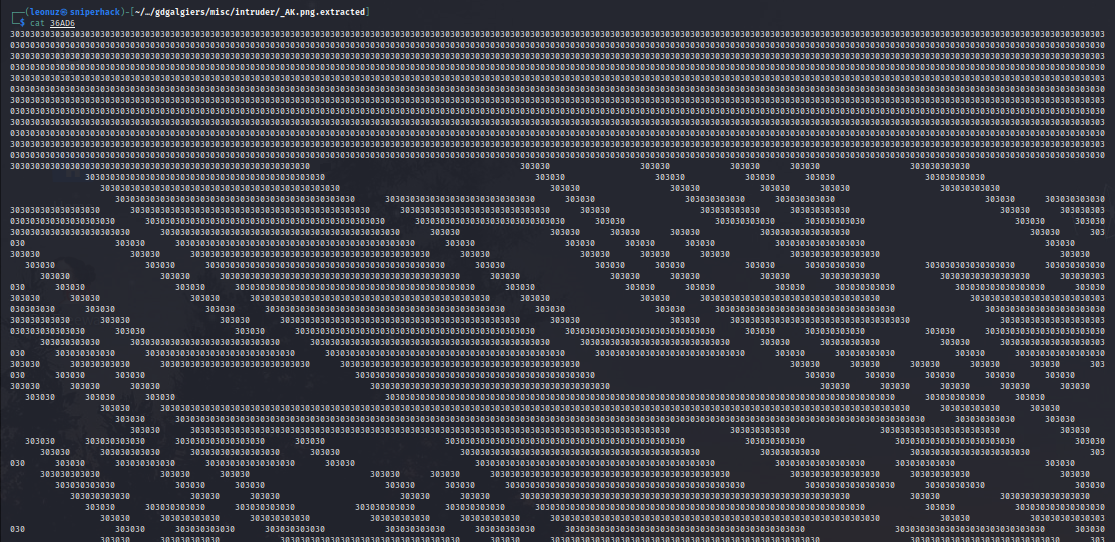
Almost there…
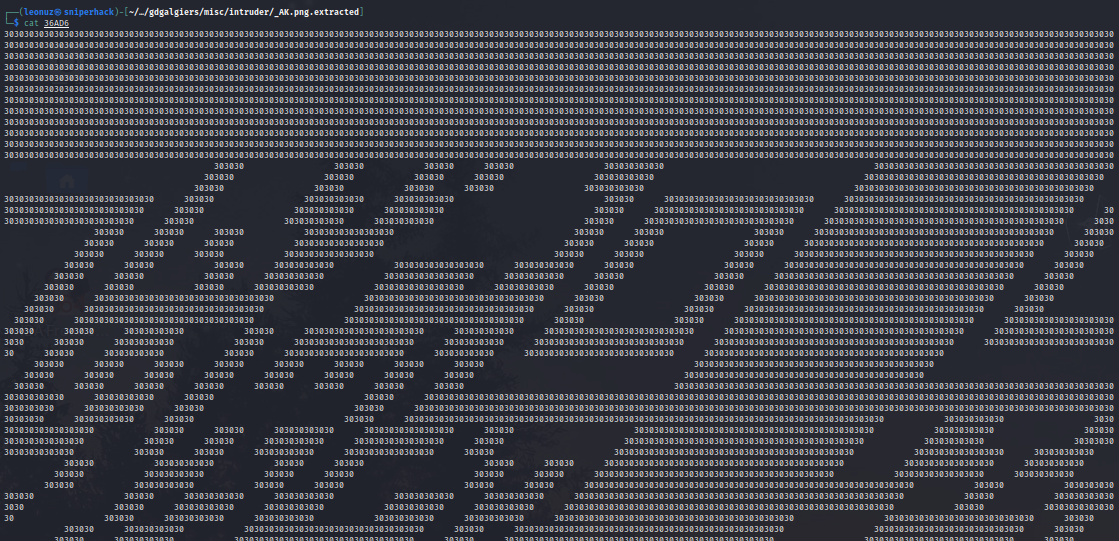
and we have the QR code!
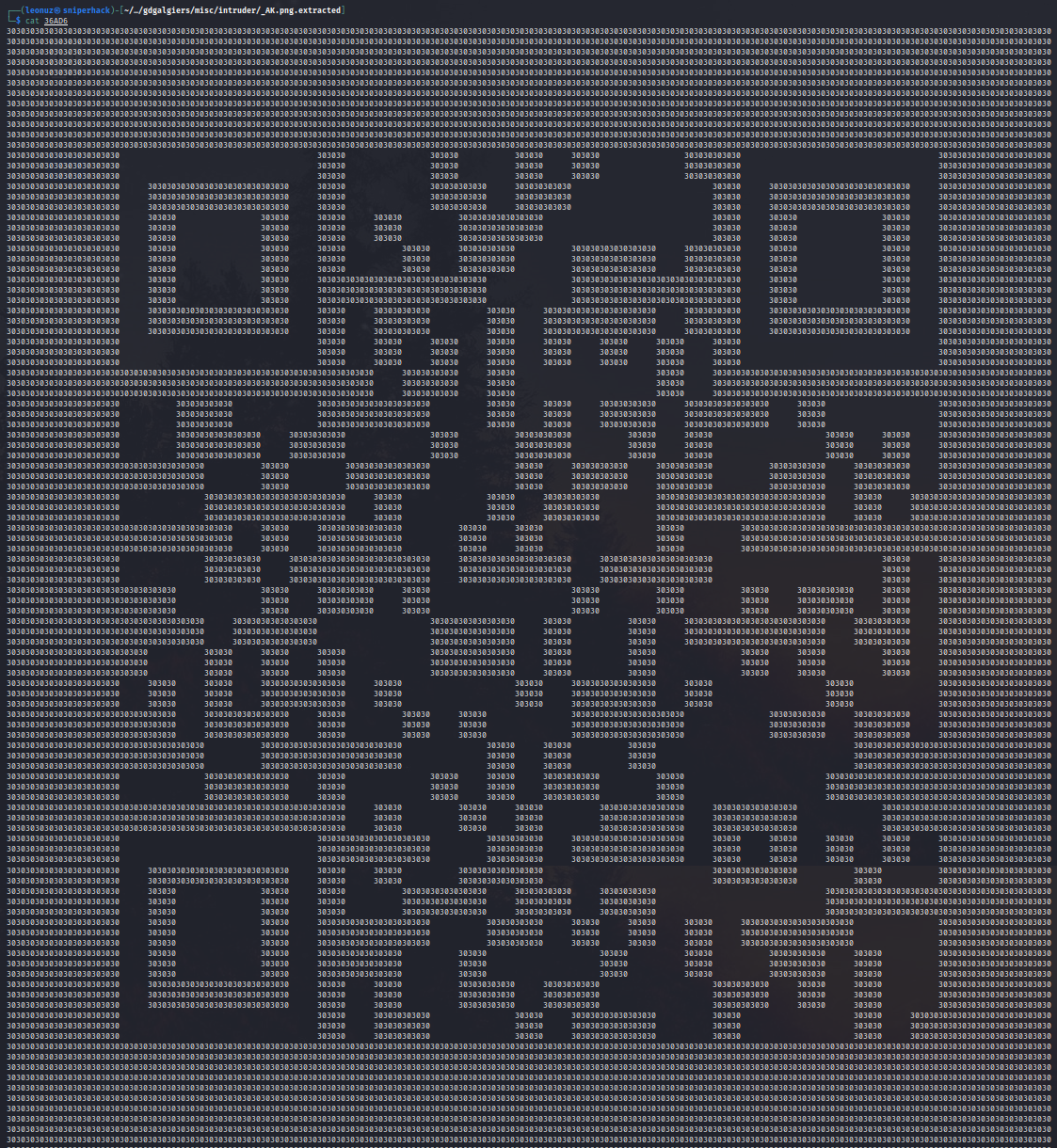
When we scan the QR code with a smartphone, we get the flag!
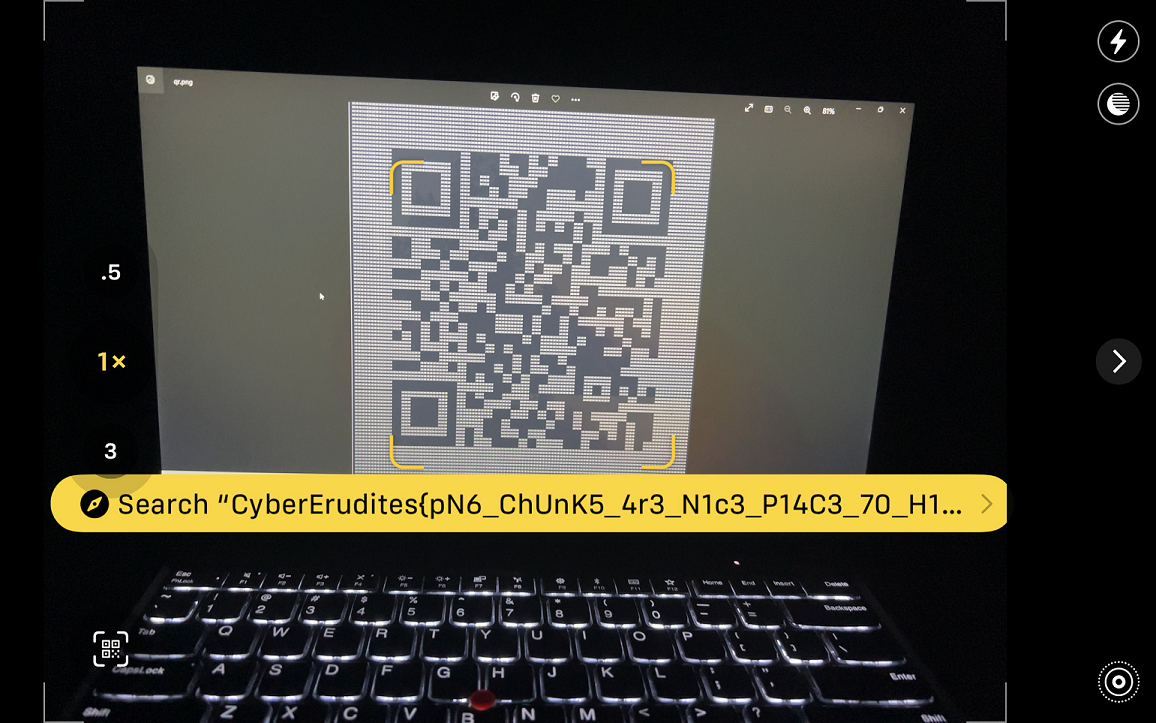
CyberErudites{pN6_ChUnK5_4r3_N1c3_P14C3_70_H1d3}
Thanks GDG Algiers, Shellmates Club and CyberErudites team for the excellent job.
Kudos to everyone who put the event together
For fun and knowledge, always think out of the box! :)

